WHEN BY DEFAULT ISN'T REALLY BY DEFAULT
Microsoft’s new “passwordless by default” is great but comes at a cost
The move is part of an industry-wide push for users to adopt passkeys.
Dan Goodin
–
May 2, 2025 4:14 pm
|
63
Credit:
Microsoft
Credit:
Microsoft
Text
settings
Story text
Size
Small
Standard
Large
Width
*
Standard
Wide
Links
Standard
Orange
* Subscribers only
Learn more
Minimize to nav
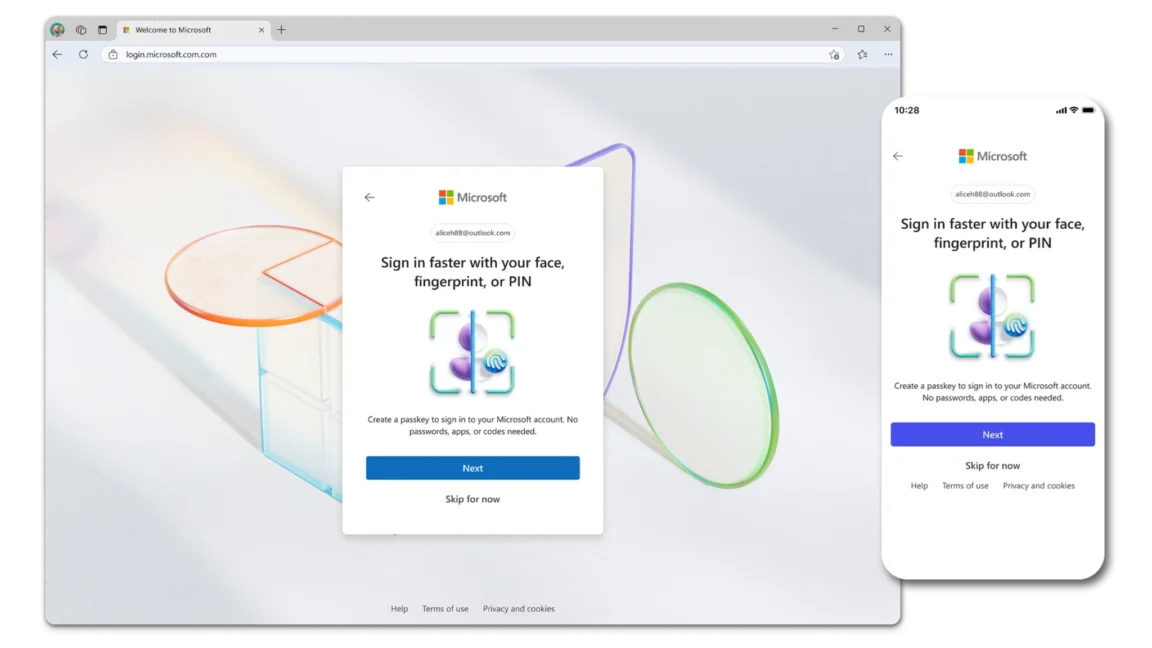
Microsoft says it’s making passwordless logins the default means for signing in to new accounts, as the company helps drive an industry-wide push to transition away from passwords and the costly security problems they have created for companies and their users.
A key part of the “passwordless by default” initiative Microsoft announced on Thursday is encouraging the use of passkeys—the new alternative to passwords that Microsoft, Google, Apple, and a large roster of other companies are developing under the coordination of the FIDO Alliance.
Going forward, Microsoft will make passkeys the default means for new users to sign in. Existing users who have yet to enroll a passkey will be presented with a prompt to do so the next time they log in.
The push to passkeys is fueled by the tremendous costs associated with passwords. Creating and managing a sufficiently long, randomly generated password for each account is a burden on many users, a difficulty that often leads to weak choices and reused passwords. Leaked passwords have also been a chronic problem.
What’s more, over the past decade, attacks such as password spraying have grown increasingly effective at breaching sensitive networks, Microsoft’s own included.
Here’s the fine print
Left out of Microsoft’s announcement is that even after users create a passkey, they can’t go passwordless until they install the Microsoft Authenticator app on their phone. Microsoft has made Authy, Google Authenticator, and similar apps incompatible, a choice that needlessly inconveniences users and undermines the whole “passwordless by default” marketing message.
Using Microsoft Authenticator isn’t a requirement for using a passkey, but account holders who don’t have it will be unable to ditch their login passwords. With a password still associated with the account, many of the security benefits of passkeys are undermined.
Passkeys, part of the FIDO Alliance’s WebAuthn standard, in theory provide a means of authentication that’s immune to credential phishing, password leaks, and password spraying. Under the latest “FIDO2” version of WebAuthn, it creates a unique public/private encryption keypair during each enrollment that’s generated and stored on a user’s phone, computer, Yubikey or similar device. In WebAuthn parlance, this device is called an "Authenticator.” The public portion of the key is sent to the account service. The private key remains bound to the user device, where it can’t be extracted.
When the user wants to log in, the account service presents a “unique challenge” that comes in the form of some random input. When the user activates the Authenticator—by entering a PIN or password or providing a fingerprint or face scan—the Authenticator uses the private key to sign the challenge and sends it to the site. The site then uses the private key it has on hand to verify the signature is valid.
The elegant design allows the person logging in to cryptographically prove they are, in fact, the authorized user without ever exposing a credential that can be stolen or otherwise compromised. Additionally, the unique keypair is cryptographically bound to the URL of the account it belongs to, making it impossible to use the credential against look-alike phishing sites. (The flow for the older FIDO1 version of WebAuthn is different.)
Microsoft accounts with Microsoft Authenticator enrolled are one of the few that offer the option to go truly passwordless. For those who aren't willing to install the app, their account will still be associated with this easily compromised shared secret. And in that case, some of the key benefits of passkeys are muted.
The FIDO Alliance tends to present passkeys as production-ready in their current state. When I covered passkeys in December, I found that they remained clumsy and difficult to use for a variety of reasons. That said, WebAuthn continues to be a work in progress and is likely to overcome its current weaknesses.
Dan Goodin
Senior Security Editor
Dan Goodin
Senior Security Editor
Dan Goodin is Senior Security Editor at Ars Technica, where he oversees coverage of malware, computer espionage, botnets, hardware hacking, encryption, and passwords. In his spare time, he enjoys gardening, cooking, and following the independent music scene. Dan is based in San Francisco. Follow him at here on Mastodon and here on Bluesky. Contact him on Signal at DanArs.82.
63 Comments